Yokai Workspace
Secure collaboration without borders
Interested in Yokai Workspace? Book a demo to see how it works.
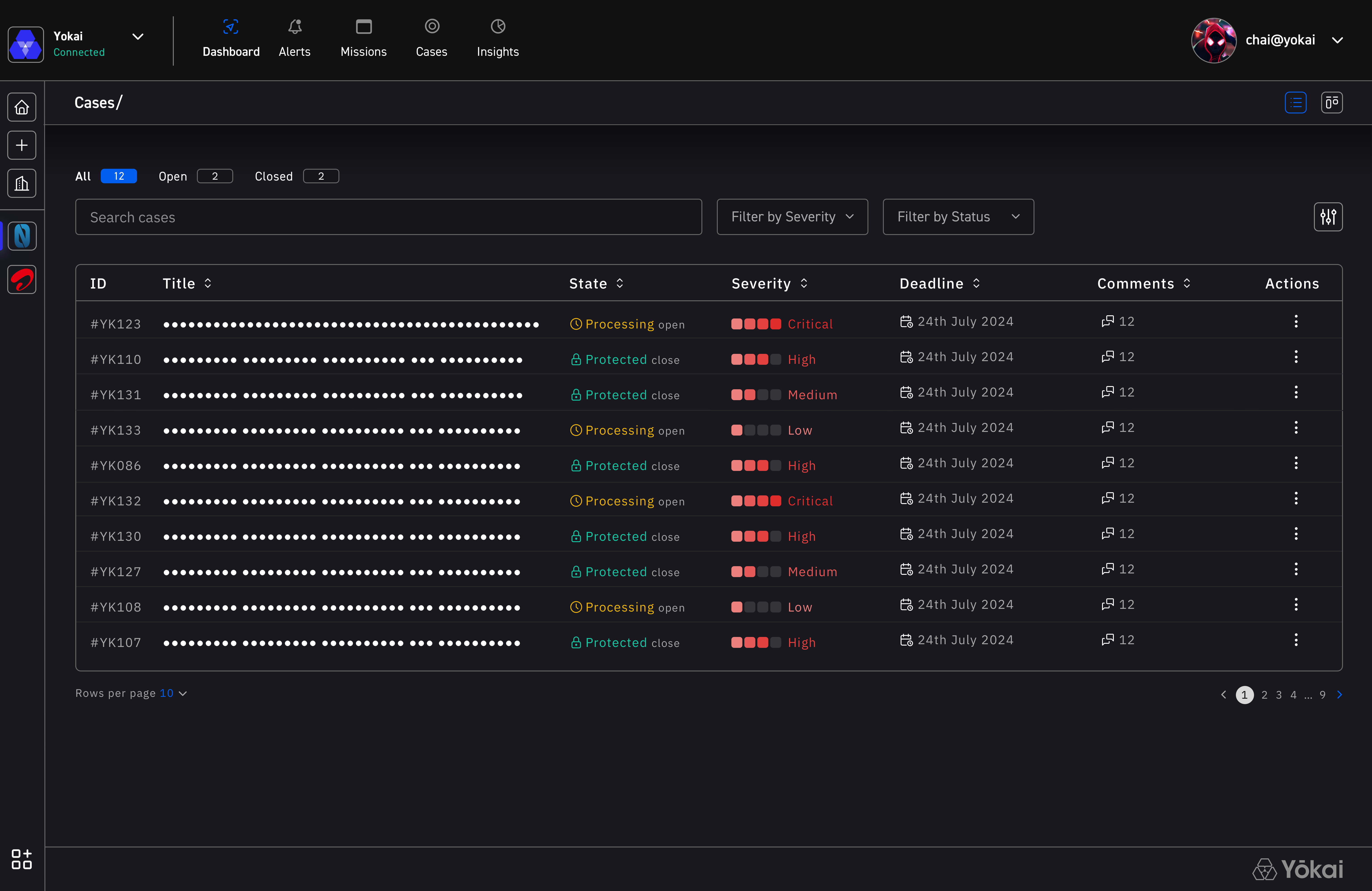
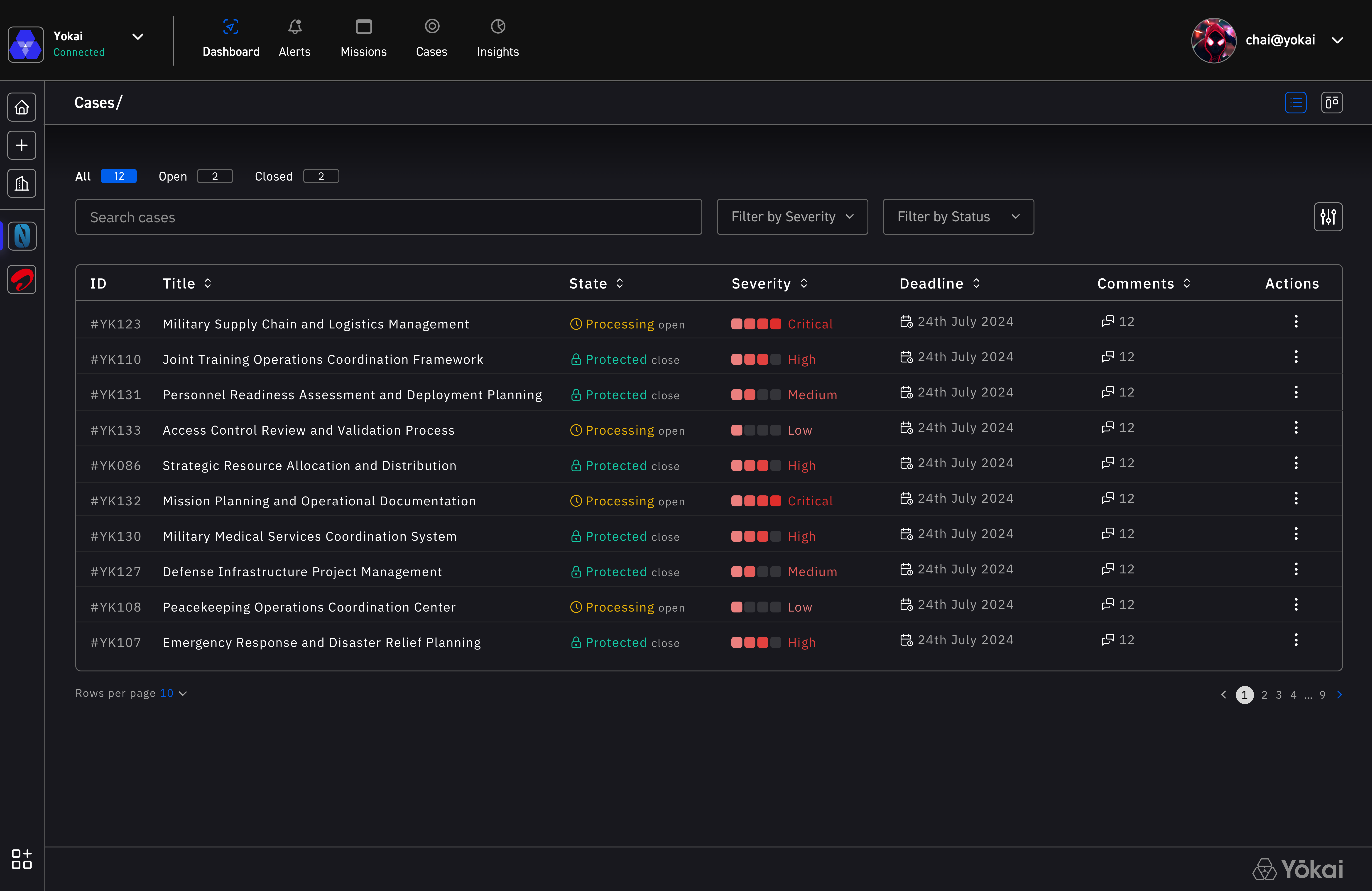
Built on Yokai Quantum, Workspace enables protected collaboration across organizational boundaries through federation. Combining true end-to-end encryption with seamless workflows, it makes secure communication effortless for finance, legal, and intelligence teams working with sensitive data.
Advancing Secure Communications
Transform your project workflows with military-grade encryption and true privacy. Keep sensitive project data protected while enabling seamless team collaboration.
True E2EE with zero-knowledge architecture ensures only you can access your data.
End-to-end encrypted project tracking and team collaboration with zero-access architecture ensuring total data sovereignty.
Perfect forward secrecy protects past communications even if keys are compromised.
Our infrastructure is designed for zero-access to user data, even by administrators.
Decentralized federation enables secure cross-organization collaboration.
Automatic key rotation and healing after potential compromises.
Flexible deployment including cloud, self-hosted and air-gapped environments.
Real-time notifications for security events and anomalies.
Security-First Project Management
Zero-Access Architecture
True end-to-end encryption ensures only authorized team members can access project data. Even system administrators cannot view your sensitive information.
Forward Secrecy
Advanced cryptographic protocols protect past communications even if keys are compromised in the future.
Post-Quantum Security
Future-proof encryption algorithms defend against emerging quantum computing threats.
End-to-End Verification
Cryptographic signatures verify the authenticity and integrity of every message and file.
Granular Access Control
Define precise permissions per team, role, and project. Control exactly who can view, edit, and manage sensitive data.
Dynamic Role Management
Easily manage roles and permissions as teams and projects evolve, without compromising security.
Zero-Trust Architecture
Every access request is verified against current permissions, with continuous authentication.
Audit Logging
Comprehensive logs track all permission changes while maintaining end-to-end encryption.
Operation Alpha
Initiative Gamma
Secure Project Spaces
Create dedicated encrypted workspaces for different missions and initiatives with complete data isolation.
Cross-Team Collaboration
Enable secure communication across teams while maintaining strict access control and data sovereignty.
Asset Management
Track and manage all mission-critical resources with military-grade encryption and granular permissions.
Secure Timeline Views
Monitor progress and coordinate activities with encrypted Gantt charts and timeline visualizations.
End-to-End Encrypted Tasks
Create and track issues with full encryption - from description to comments and attachments.
Custom Workflows
Design secure workflows that match your processes while maintaining zero-knowledge encryption.
Protected Attachments
Share files and documents with automatic encryption and granular access controls.
Secure Dependencies
Link and track related issues while maintaining complete data isolation and privacy.
Privacy-Preserving Metrics
Generate insights and reports while maintaining end-to-end encryption of underlying data.
Secure Dashboards
Create custom views with real-time metrics, protected by role-based access control.
Encrypted Exports
Export reports and data with maintained encryption and granular permissions.
Progress Tracking
Monitor team and project performance without compromising data privacy.
Ready to get started with Yokai Workspace?
Book a demo to see how Yokai Workspace can transform your team's collaboration.
